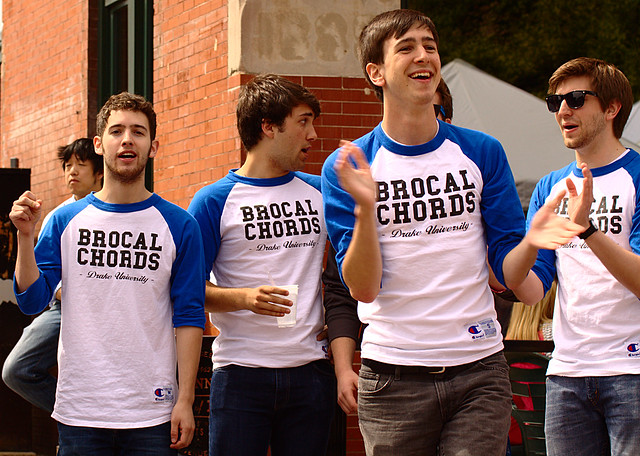First set of VMworld 2012 / SFO photos. Please see the full Flickr set for more.





Update #3: I’ve had zero time to work on my photos. Had a family emergency over the Labor Day Weekend (not fun calling 911 on Saturday). Photos coming soon, I promise! Please check back.
Here’s a teaser photo from the VMworld 2012 Party last night. There will be many more photos to come, so please check back!
Has the smart phone supplanted the Zippo? Empirical evidence provided.
 Here’s the Ghandi statue in the Ferry Building parking lot:
Here’s the Ghandi statue in the Ferry Building parking lot:
The VMware View 5.1 Installation Guide recommends replacing the default self-signed SSL certificates on all servers (Connection, Security, and Composer) with a certificate signed by a Certificate Authority (CA). For the externally-facing Security server role, you should purchase a signed cert from an established CA provider. For your internal Connection and Composer servers, however, it makes more sense to deploy an internal CA.
The other day, myself and a co-worker ran into a situation where we had configured Microsoft’s CA server on a Windows Server 2008 Enterprise server, but were having issues getting the Connection servers to connect to it and generate a certificate request (CSR). After spending too much time trying to get past the RPC error, I decided to by-pass that process by using openssl on an ancient MacBook Pro to generate the CSR.
The following is an account of the process I used, noting some of the pitfalls that hung me up along the way and providing references to Web sites which were helpful.
Here are some of the ways I messed up along the way, causing myself more grief than was necessary:
As you may know, the session catalog for VMWorld 2012 came out a few days ago. I just took a few moments to peruse the catalog and pick out a list of sessions I though sounded interesting. I still need to prioritize and weed out this list before session registration begins. I will also need to reconcile the sessions I attend with my desire to complete a lot more of the hands on lab sessions than I did at VMWorld 2010. I’m hoping to be more of a lab rat this time around!
In no particular order, here are the sessions on my list so far:
If you plan on going, but haven’t registered yet, hop to it!
Just had to whip out a quick blog post about my experience installing the dead-simple Yubikey plugin for WordPress. It really is as easy as the Installation page states:
I only had one issue, but it was minor. After installing the plugin per the directions above, my login screen had a message stating that Yubikey authentication was disabled because I was missing the PHP Curl and Hash modules. A quick ‘sudo apt-get install php5-curl phg5-mhash; sudo /etc/init.d/apache2 restart’ later, and I was good to go!
Finally, the updated URL for generating a Yubico API key. You need to complete step 1 first, however, because you’ll need to provide an OTP and an e-mail address to generate the API key.
It has been awhile. I didn’t get too many photos from this Farmers Market.
As always, please visit my Flickr Set, or click on each photo below to go directly to it on Flickr. Please share and enjoy these photos, and remember that they are licensed under the Creative Commons Attribution, Non-Commercial, Share Alike (BY-NC-SA) license.


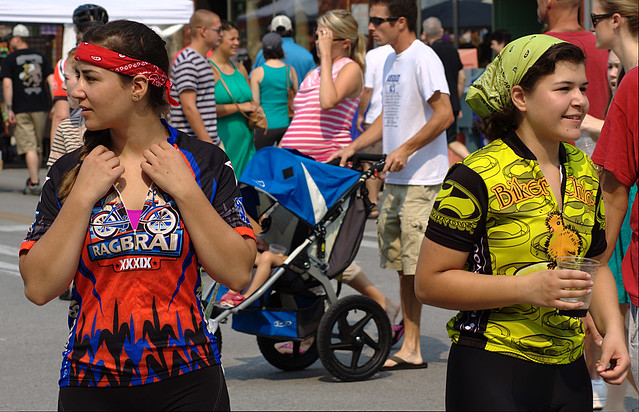
Our third Farmers’ Market of the 2012 season, and another super crowd. This was also the second annual Des Moines Flickr Friend Photowalk. Be sure to check out the other amazing photos there.
As always, please visit my Flickr Set for more photos (there are 23 in this set), or click on each photo below to go directly to it on Flickr. You can also skip straight to the slide show if you’d like. Please share and enjoy these photos, and remember that they are licensed under the Creative Commons Attribution, Non-Commercial, Share Alike (BY-NC-SA) license.




Not too many photos this time, so they are all posted here. Please visit my Flickr Photostream or skip directly to the slideshow for my latest photos. To view larger versions on Flickr, just click an image.
As always, these photos are licensed under the Creative Commons Attribution, Non-Commercial, Share Alike (BY-NC-SA) license.




Our second Farmers’ Market of the 2012 season, and another great crowd. This time, I got some wonderful photos of the talented Brocal Chords vocal group performing on the street corner. I was also able to capture several couples strolling the market.
As always, please visit my Flickr Set for more photos (there are 19 in total), or click on each photo below to go directly to it on Flickr. You can also skip straight to the slide show if you’d like. Please share and enjoy these photos, and remember that they are licensed under the Creative Commons Attribution, Non-Commercial, Share Alike (BY-NC-SA) license.